Zenith Defense
Support Consulting
- Product and Vendors
- Mira Security
Cyber Security
Detect. Decrypt. Deter. Encrypted Traffic Orchestration without Compromise
Mira provides safe and secure visibility into encrypted traffic allowing the tools used by enterprise security teams to function effectively
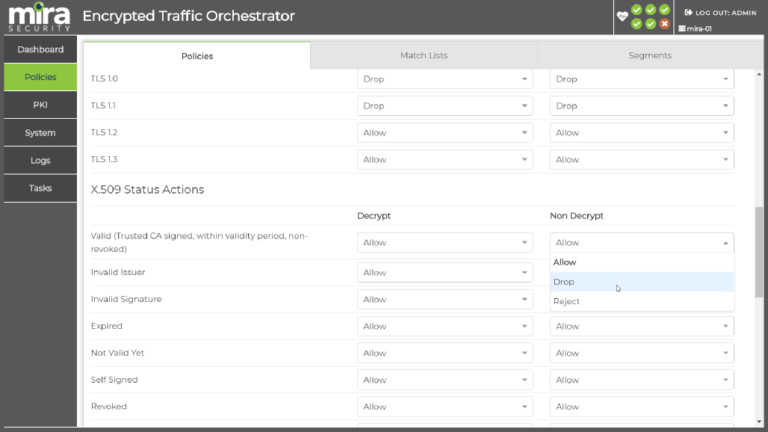
MIRA FEATURES
Mira ETO software enables the enterprise security stack to detect and mitigate threats while ensuring that privacy and compliance requirements can be met.
- Automatically detect all SSL/TLS and SSH traffic in the network, no matter what ports are being used
- Capable of decrypting SSL v3, TLS 1.0, 1.1, 1.2 and 1.3, as well as SSHv2
- Transparent to the higher-level protocols being carried on top of the encrypted layer providing decrypted flows to security tools for any existing or future protocols
Mira provides safe and secure visibility into encrypted traffic allowing the tools used by enterprise security teams to function effectively
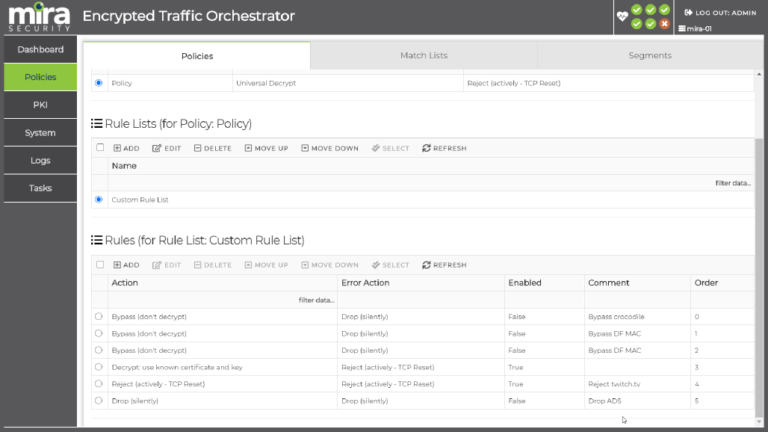
Mira seamlessly integrates with existing security tools to protect your investments
- Policy control over which encrypted traffic is made visible allows compliance with industry requirements and enterprise policies on data privacy
- Policy control over which encryption mechanisms are allowed in the enterprise network to prevent weak or obsolete methods from being used
- Comprehensive logging enables the enterprise to analyse encrypted traffic within the network and derive actionable changes to operational policy
- Scaling from a sub 1G for branch offices and micro edge locations to nearly 100G allows for growth and supports the collapsing of data centers.


