Support Consulting
Cyber Security
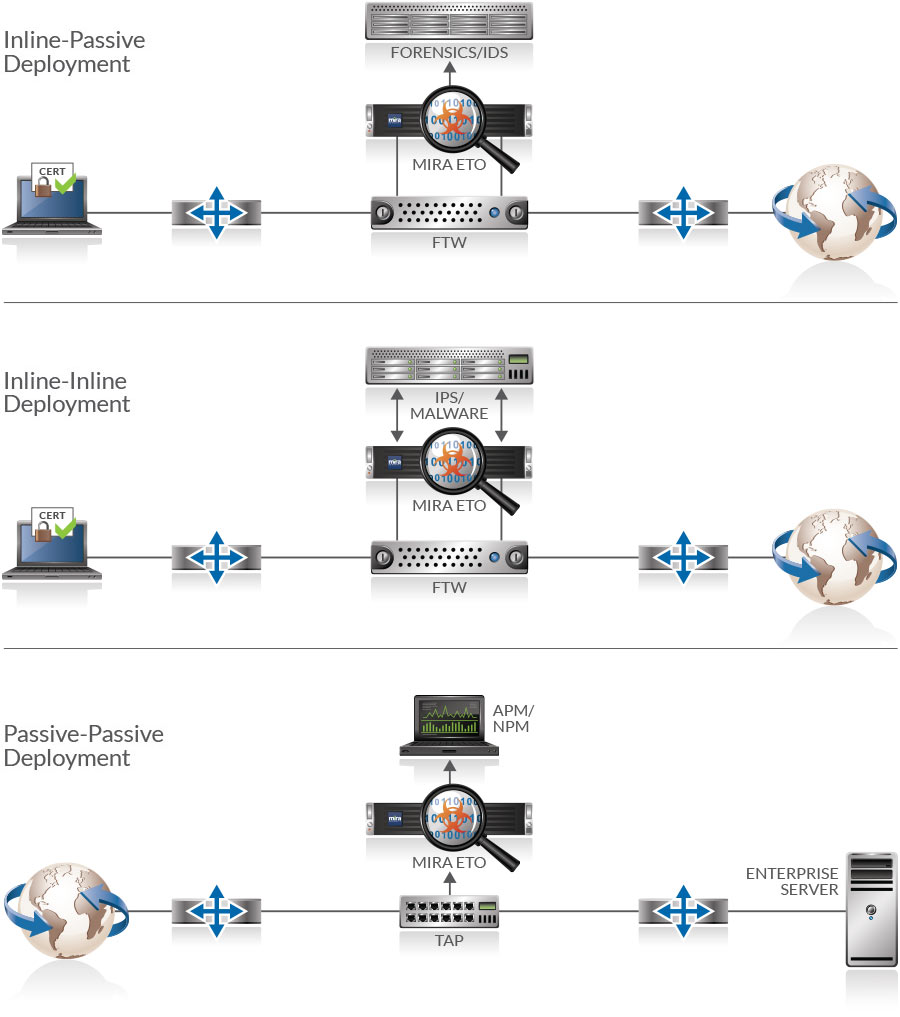
How Mira Works
Mira Encrypted Traffic Orchestration (ETO) automatically detects SSL, TLS and SSH traffic and feeds it to one or more security tools that detect and mitigate any threats that may be present. No special interfaces or software changes are required to the security tools. They simply receive traffic from Mira ETO as if it was traffic directly from the network. This means the existing security stacks can regain their effectiveness, diminished by the increase in encrypted traffic, simply by deploying Mira ETO to feed them.
MIRA DEPLOYMENT MODES
Enterprises need to balance security risks of not decrypting traffic with the privacy implications of doing so. Mira ETO provides the flexible policy controls to ensure that balance is achieved.
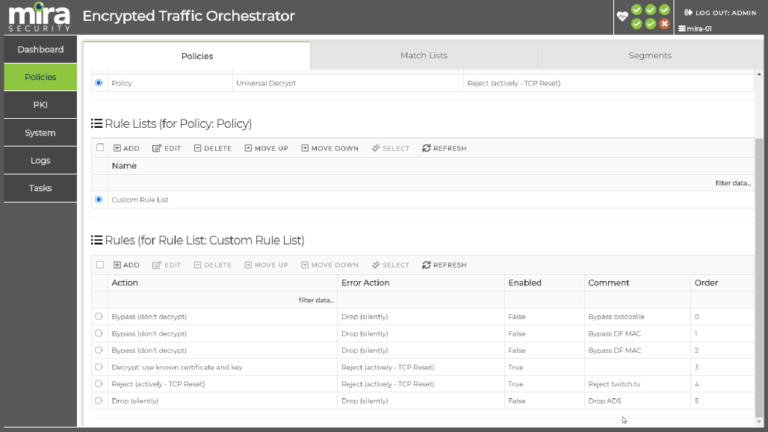
Flexible policy control features of Mira ETO enable enterprises to enforce policy on what encryption mechanisms are allowed in order to ensure a secure environment. For encrypted traffic that is allowed, there are fine-grained policies that enable control over which encrypted flows are decrypted and made visible to security tools. Policy controls can optionally make use of the Mira category database and/or a locally created category database to determine which types of traffic are decrypted.
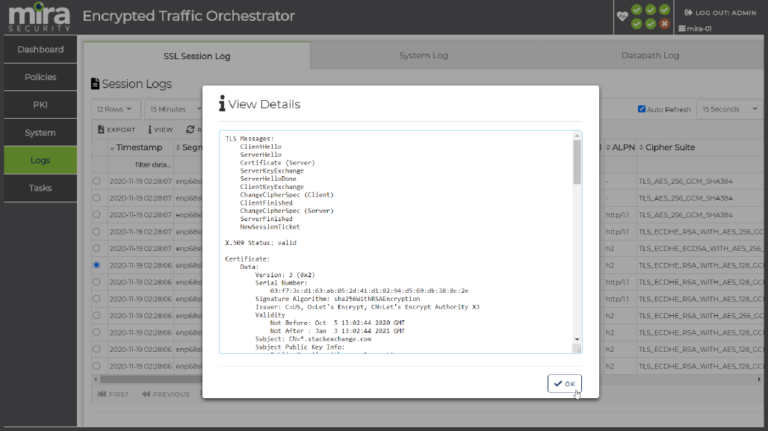
Mira ETO software is designed for high-performance decryption and can work with link speeds of 1, 10, 25, 40 and soon 100 Gbps, providing decryption for anywhere from <1 Gbps of encrypted traffic up to >100 Gbps. Mira’s ETO software supports high rates of new TLS handshakes per second, ensuring that there is no performance impact when deployed. The software is architected to allow the use of external hardware PKI engines enabling both decryption performance and new handshake performance to be scaled even higher.


